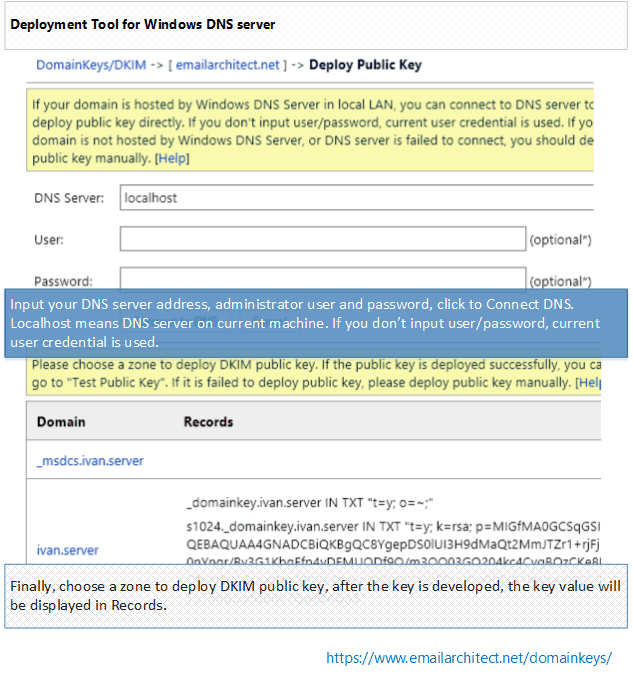
If your domain is hosted by Windows DNS Server in local LAN. After you added a domain in DKIM Plugin Manager, you can select the domain and click "Deploy Key", input your DNS server address and choose the DNS zone, the public key will be deployed to DNS server automatically.
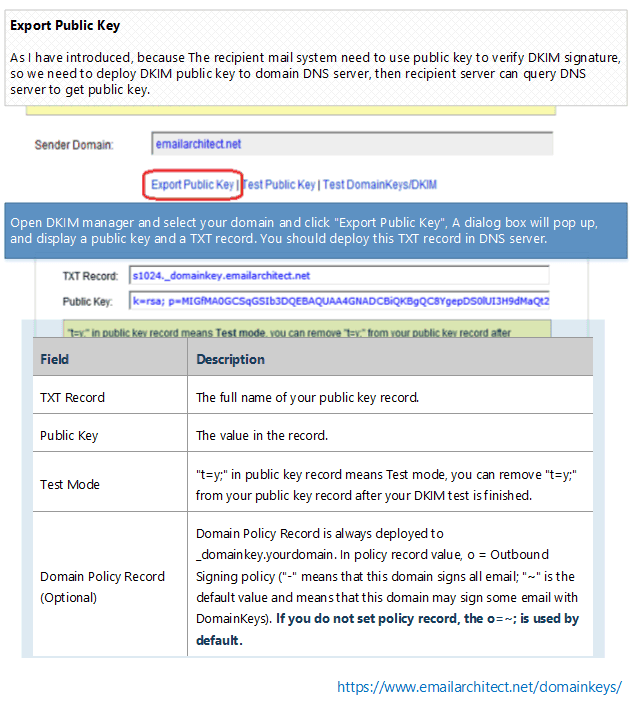
If your domain is not hosted by Windows DNS server in local LAN, or it is failed by "Deploy Key" in DKIM manager, you can select the domain and click "Export Public Key". A dialog box will pop up and display a Public Key and a TXT record for deployment in your DNS server.
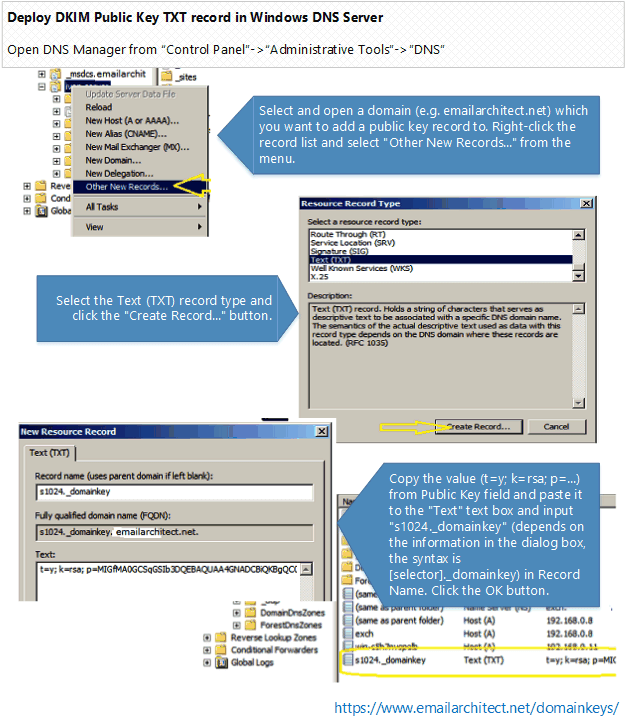

If you're using Windows 2000 DNS server, you should create "_domainkey" domain under "your domain" at the beginning, and then create "s1024" TXT record under "_domainkey" sub-domain. The reason is that creating "s1024._domainkey" TXT record directly is not permitted in Windows 2000 DNS server.
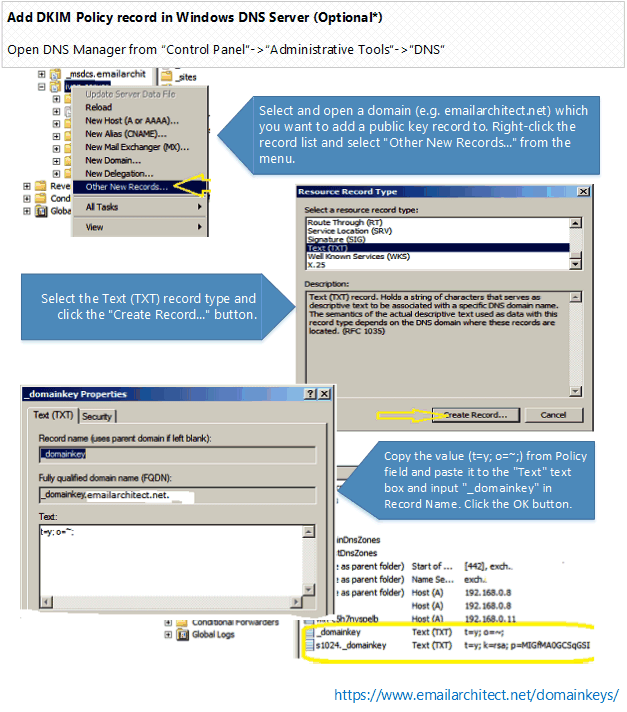
*This record is optional, you don't have to add it. If you do not set policy record, the o=~; is used by default.
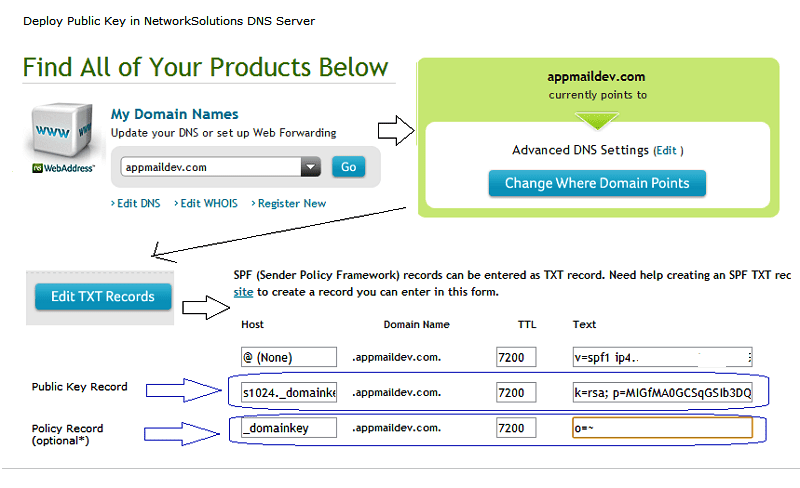
If your domain is hosted by www.networksolutions.com, you can deploy your public key like this:
If your domain is hosted by GoDaddy, you can deploy your public key like this:
If your domain is hosted by Bind DNS server, you can add DKIM public key record like this: locate your domain's zone file and open it with your preferred editor, then add the following content:
; DKIM policy record _domainkey.yourdomain.com. IN TXT "o=~;" ; DKIM public key record s1024._domainkey.yourdomain.com. IN TXT "v=DKIM1; k=rsa;p=MIGfMA0GCS....ofIz0IW7QwIDAQAB"
If your domain is hosted by other ISP, as most ISP provide DNS Web administration like "network solutions" do, you can refer to "Deploy Public Key TXT in Network Solutions DNS server" section and deploy your public key in your ISP DNS Web administrative tool.
If you are not DNS server administrator, or your domain is hosted by other DNS server, please send the information in dialog box -> DNS Public Deployment to your domain DNS server administrator for assistant.
After the Public Key in DNS server is deployed, you can click "Test Public Key" in EA DomainKeys/DKIM Manager to verify the public key. It will tell if your public key is deployed correctly. After your public key is ok, you can go to " Test DomainKeys/DKIM signature".
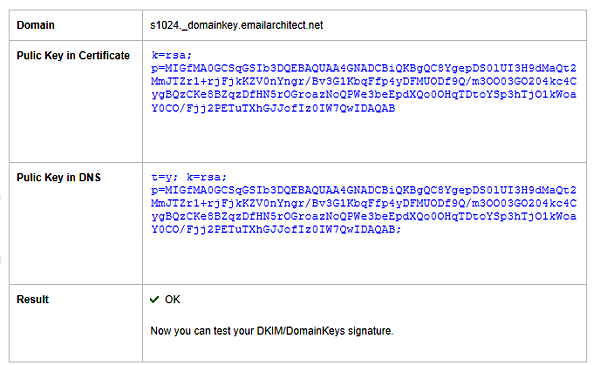
You can also use nslookup command to test your public key as follows:
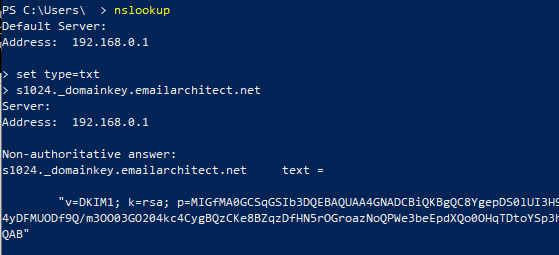
Windows Start menu -> input:
nslookup
press enter
input:
set type=txt
press enter
input ([selector]._domainkey.yourdomain):
s1024._domainkey.yourdomain
If your key is deployed successfully, it should return something like above screenshot.
>> Test DomainKeys/DKIM signature
Because single DNS TXT record is limited to 255 characters, public key length of 2048 certificate exceeds the limit. So you need to separate public key to two parts in DNS server.
In Windows DNS Server, you should use line-break to separate the long public key
v=DKIM1; k=rsa; p=k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC8YgepDS0lUI3H9dMaQt2Mm... JTZr1+rjFjkKZV0nYngr/Bv3G1KbqFfp4yDFMUODf9Q/m3OO03GO204kc4CygBQzCKe8BZqzDfHN5rOG...;
In BIND Server, you should deploy key as follows:
s1024._domainkey.yourdomain.com. IN TXT ("v=DKIM1; k=rsa; p=MIIBIjANBgkqG9w0BAQEFAAOCAQ8AMIIBCg..."
"2LjDmbvj6V82iSnW3lAg3Sr212oKm7iFAT6diDvItD5botwDpk9jrRFxi...")
;OR
s1024._domainkey.yourdomain.com. IN TXT "v=DKIM1; k=rsa; p=MIIBIjANhkiG9w..." "2LjDmbvj6iSnW3g3Sr212o4..."
See Also
Setup DomainKeys/DKIM
Test DomainKeys/DKIM signature
Troubleshooting
Using Selector
Using Sender Rule
Server Core and Installer Command Arguments
Appendix - Set up SPF record in DNS server
Appendix - Set up DMARC record
Appendix - DKIM/SPF/DMARC Inbound Authentication in Exchange Server
Appendix - Use DkimPowerShell Module in PowerShell
Online
DKIM in IIS SMTP Service - Tutorial
DKIM in Exchange Server 2003 - Tutorial
DKIM in Exchange Server 2007/2010/2013/2016/2019 - Tutorial
DKIM/SPF/DMARC Inbound Authentication in Exchange Server
Bulk Email Sender Guidelines